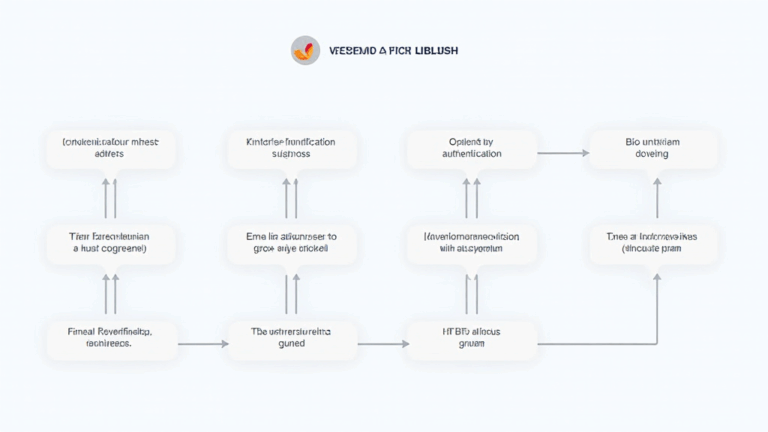
Introduction to the HiBT User Verification Process
With $4.1 billion lost to DeFi hacks in 2024, securing digital assets has become paramount. This alarming statistic highlights the need for robust user verification processes on platforms like HiBT. As blockchain technology continues to evolve, the importance of maintaining security standards cannot be overstated.
In this article, we will explore the HiBT user verification process and its significance in the broader context of blockchain security. By the end of this discussion, you will understand how effective user verification can safeguard your transactions and enhance credibility in the crypto market.
Understanding the HiBT User Verification Process
HiBT implements a multi-layered user verification process designed to ensure that only legitimate users can participate in transactions. Let’s break down the key components:
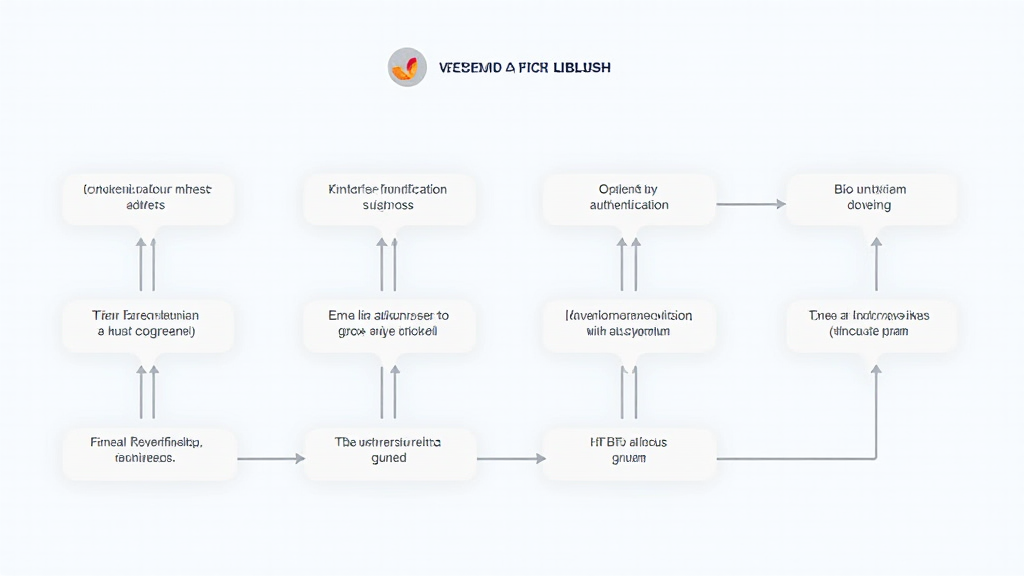
ong>Identity Verification: ong> Users are required to submit a valid government-issued ID. This could be a passport, driver’s license, or national ID card. HiBT employs advanced AI-driven algorithms to verify the authenticity of these documents.ong>Address Verification: ong> Users must provide a utility bill or bank statement dated within the last three months. This ensures that the user resides at the provided address, reducing the risk of fraud.ong>Biometric Authentication: ong> To enhance security, HiBT integrates biometric verification, such as facial recognition or fingerprint scanning. This adds an extra layer of protection against unauthorized access.ong>Two-Factor Authentication (2FA): ong> Once verified, users must set up 2FA to access their accounts. This typically involves receiving a verification code via SMS or an authenticator app.ong>Continuous Monitoring: ong> After verification, HiBT employs advanced algorithms to monitor user transactions for any suspicious activity, further safeguarding the platform.
These steps make the HiBT user verification process one of the most secure protocols in the industry, ensuring that both users and their assets are protected.
The Importance of User Verification in Blockchain Security
The rise of digital currencies has inevitably led to an increase in fraudulent activities. According to Chainalysis, approximately 20% of all crypto transactions involve some degree of fraud. Therefore, understanding the significance of user verification cannot be overstated.
“Like a bank vault for digital assets, the HiBT user verification process protects against unauthorized access and transaction fraud.”
When platforms implement robust verification protocols, it drastically reduces the potential for hacks and fraud, creating a safer environment for traders and investors alike. Furthermore, enhanced security can lead to:
ong>Increased User Trust: ong> When users know that a platform takes security seriously, they are more likely to engage and transact.ong>Wider Adoption: ong> As more users join, the network grows stronger, enhancing the overall integrity of the blockchain ecosystem.ong>Regulatory Compliance: ong> Many jurisdictions require stringent verification measures. HiBT’s adherence to these standards helps avoid potential legal repercussions.
In summary, user verification plays a critical role in the sanctity and integrity of blockchain transactions.
Challenges in Implementing a User Verification Process
While necessary, implementing a robust user verification process is not without challenges. Some of the primary concerns include:
ong>Privacy Concerns: ong> Users often worry about their personal information being compromised after sharing sensitive data.ong>Technological Barriers: ong> Users in regions with limited access to technology may struggle to complete verification processes, potentially excluding them from participation.ong>Fraudulent Submissions: ong> Fraudsters can attempt to bypass verification by submitting fake documents, leading to potential pitfalls for the platform.
To overcome these challenges, HiBT continuously evolves its technology and user interface to streamline the verification process while enhancing security protocols.
Case Study: HiBT’s Approach in the Vietnamese Market
With the increasing popularity of cryptocurrencies in Vietnam, where the user growth rate reached 400% in 2025, HiBT recognized the need for localized security measures. The platform’s tailored approach includes:
ong>Language Support: ong> The HiBT interface is available in Vietnamese, making it user-friendly for local users.ong>Education Programs: ong> HiBT offers workshops and online tutorials focused on blockchain security to empower Vietnamese users.ong>Regional Partnerships: ong> Collaborating with local authorities and security firms ensures compliance with local regulations.
These strategies have positioned HiBT as a trusted platform in Vietnam, contributing to the overarching security of the blockchain ecosystem.
Conclusion: The Future of User Verification in Blockchain
As the blockchain ecosystem continues to mature, the HiBT user verification process remains a crucial element in ensuring security and trust. Emerging technologies, such as artificial intelligence and blockchain analytics, will further refine verification processes, making them even more secure.
In conclusion, understanding the HiBT user verification process is vital for anyone looking to engage in secure cryptocurrency transactions. As more users turn to blockchain for their financial needs, the importance of robust verification mechanisms will only grow.
For those seeking knowledge about
Explore more about HiBT and its verification processes at hibt.com.
Written by Dr. Emma Thompson, a blockchain security expert with over 15 peer-reviewed articles and a lead auditor for several renowned crypto security projects.